Introduction
If you need to give multiple people access to one of your GridPane-hosted websites, and these require separate login details, this now possible via your GridPane dashboard.
Your websites are owned by a “primary” system user, and this article will walk you through adding what we call Restricted Alias system users to you site with path restrictions in their chroot.
Information
This is only available on the Ubuntu 22.04, 24.04, and future stacks, as it requires their shared chroot set up.
Settings and Restrictions
There are rules that both primary system users (site owners) and restricted alias system users follow (detailed below), and in a nutshell, they are NOT interchangeable. They each function completely differently, and you cannot swap/alter their purpose.
Restrictions
- Restricted alias users belong to a “primary” system user – the one with its own group, and they can’t be moved from one primary user to another.
- Restricted alias users cannot own sites.
- Restricted alias users are locked to single sites/paths and these cannot be updated after creation.
- A primary system user, with restricted aliases, can not own more than one site at a time.
- You cannot swap a primary user to a restricted alias user and vice versa.
Websites and Restricted Alias System Users
- If you change a website’s system user, all the restricted alias users are deleted, since they were locked to that site/path.
- Deleting a site with a primary system user with aliases as the owner will delete all the restricted alias users prior to deleting the primary system user.
- Building sites with a restricted alias user is not allowed.
Domain Swaps and Restricted Alias System
Domain swaps work same as swapping over a websites system user – all attached alias system users are removed during the domain swap, since their paths will become invalid.
Step 1. Create the New System User
Head over to the Sites page within your GridPane account and click on the website that you want to create an additional system user. This will to open up the website customizer, and from there you can select the System Users tab:
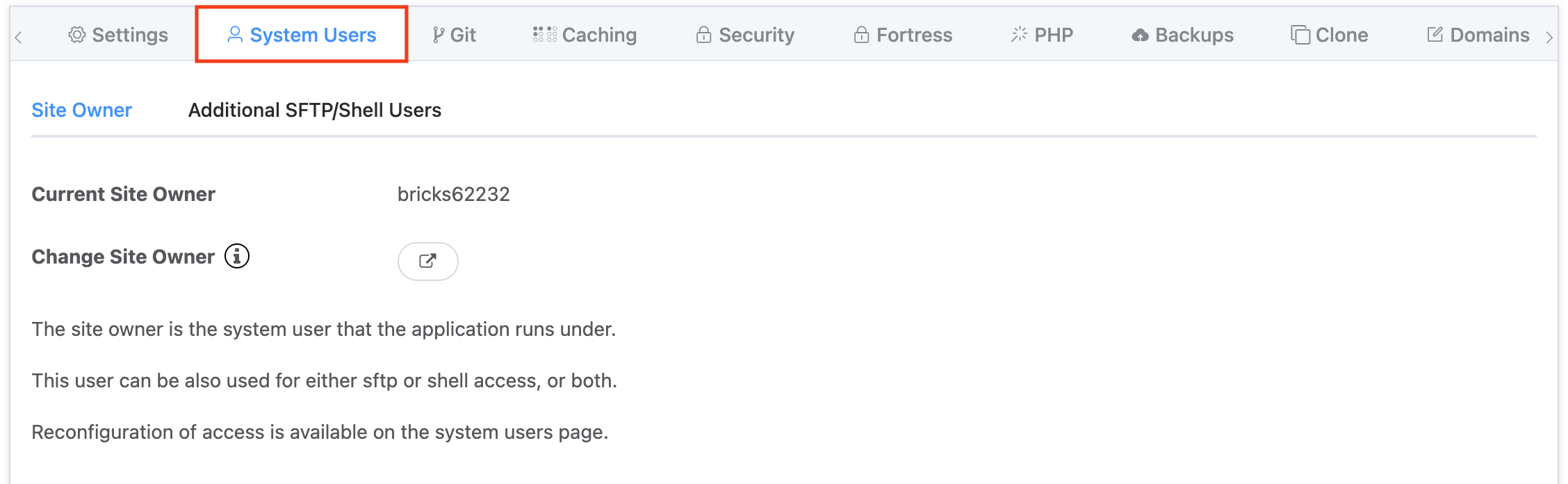
Then click through to the Additional SFTP/Shell Users tab and click on the Add New SFTP/Shell User button:
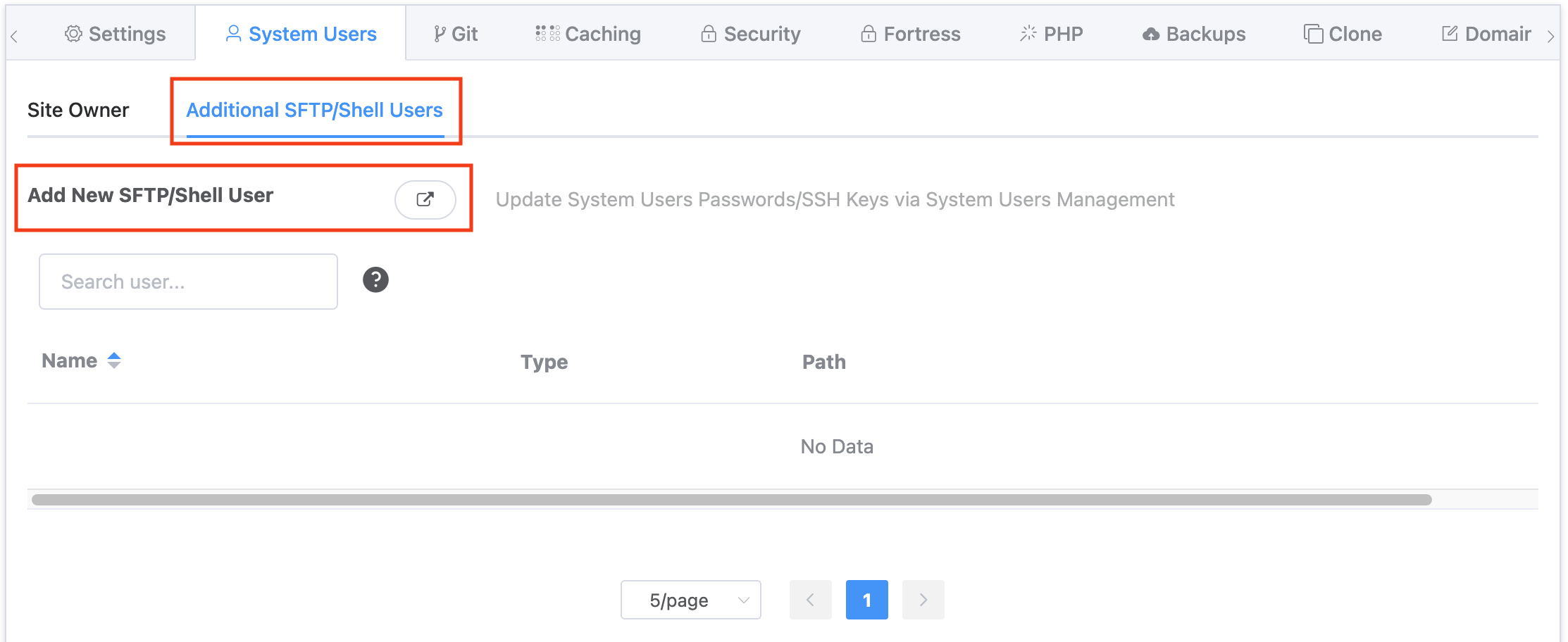
Step 2. Configure the System User
You have 2 options for your new restricted alias user:
- You can give the user full site access.
- You can restrict the user to a specific path, giving partial access to the websites files instead of full access.
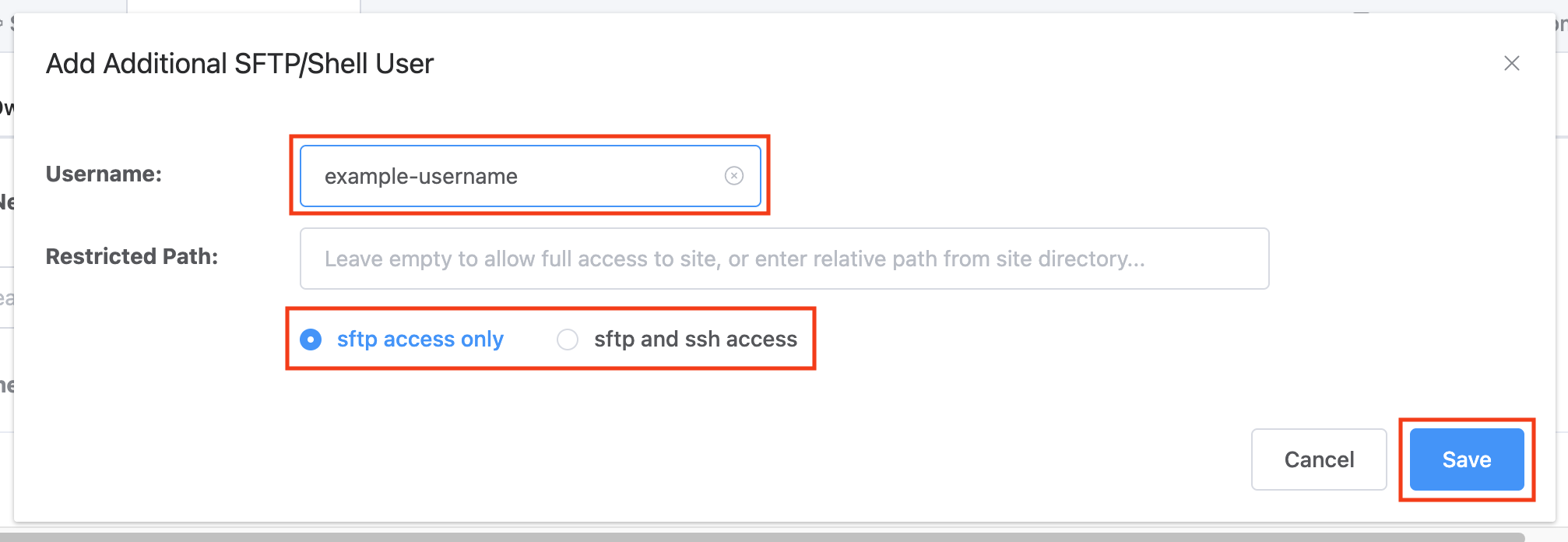
Option 1. Full Access
This option will allow full access your chosen site. Simply enter your system user name, and then choose the SFTP / SFTP+SSH option, and hit the save button:
Option 2: Restricted Access
In many scenarios, granting full access will not be needed or desired. Here are a few examples of how you could restrict access to specific paths:
/example.com/htdocs
/example.com/htdocs/wp-content
/example.com/htdocs/wp-content/plugins
In the above paths, you can restrict a user to the WordPress installation (minus the wp-config.php file), only the files within the /wp-content directory, or only the websites /plugin directory.
As a rule of thumb, you should only grant access to the files your team or client need to access.
Here’s an example of how this looks when creating a restricted alias system user with a restricted path within the UI:
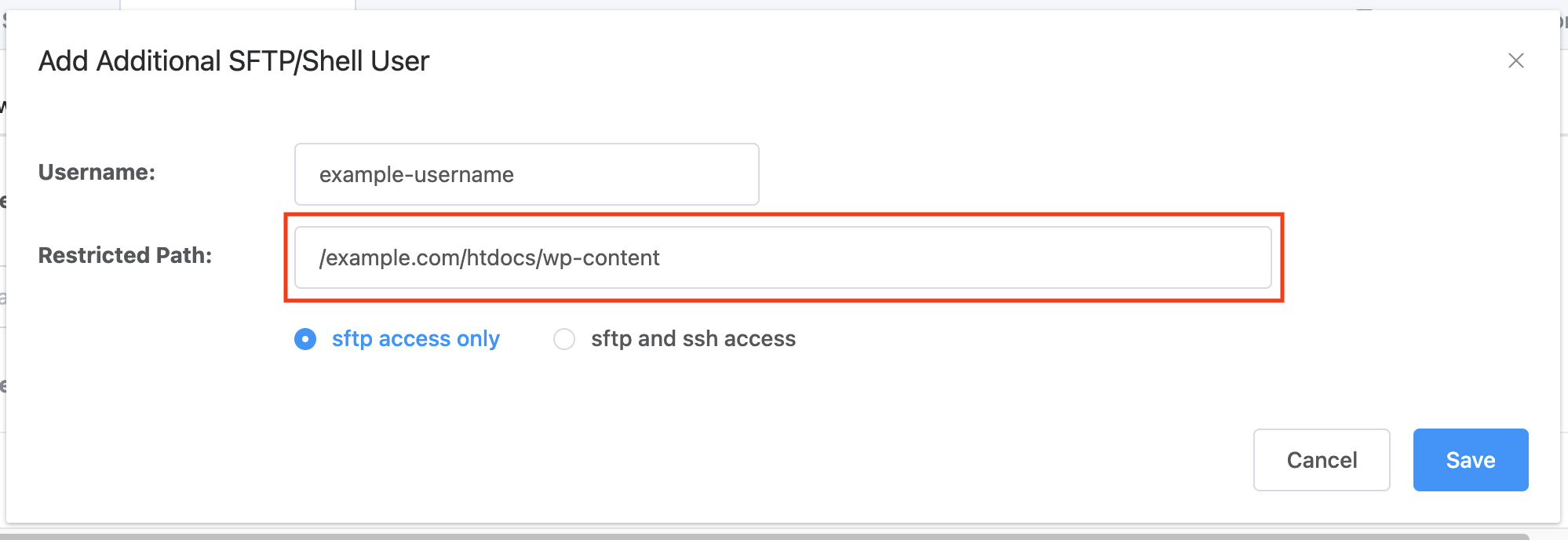
Once you’ve set your name, path, and access type, click the Save button, and you’re new system user is all set.
