Introduction
Dealing with malware is a task for an experienced security professional. This article offers some tips for your first steps when dealing with a site that has been compromised with malware.
Table of Contents
Our Recommendation: Hire a Professional
Very few people have a deep enough understanding of WordPress security to locate and clean up malware effectively, and due to this, we always recommend that you consult a professional who can help with the following:
- Root cause analysis – identifying how your website was compromised in the first place so that you prevent it from happening again.
- Codebase and database malware scanning with a secure, server-level scanner that has an exhaustive and up-to-date signature database.
- Effective malware cleanup.
Thomas Raef of WeWatchYourWebsite.com is a popular choice within the GridPane community and other Facebook communities.
Your Website Has Been Compromised: First Steps
If you have a website that’s been infected with Malware, these are a few precautionary steps to prevent SEO penalties and browser warnings.
Ensure the website is on its own system user
The first thing to do is make sure there are no other websites that are on the same system user – if there are, move them to their own system user immediately.
This is unlikely to be the case now that our default settings
Disable public access to the site
Taking your website offline immediately will help prevent SEO penalties and will protect your business and website visitors.
You can quickly make your site inaccessible by turning on HTTP Authentication via your website customizer:
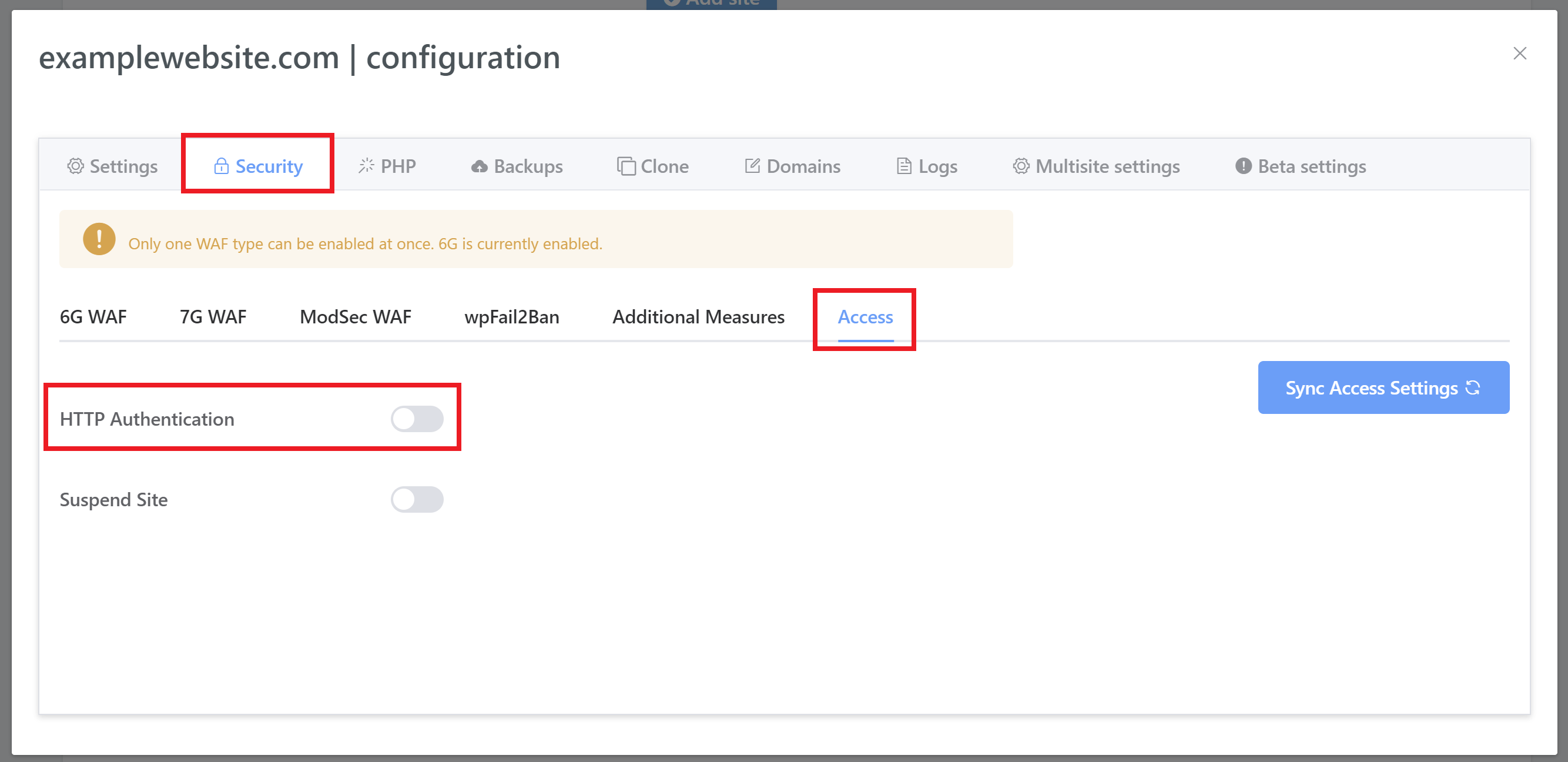
A good option after this is to create a new site temporarily on a different server and set up a maintenance/holding page, and change the site’s DNS to point to this temporary site.
Once that’s done, you can access the hacked site via a local host redirect while you clean it up and/or move the website elsewhere for diagnosis. Once the site is safe and ready for traffic again, you can change the DNS back.
Budget Quick Fix: Use a Backup
This is not an ideal solution, as you may not be able to determine how your website was compromised in the first place. However, you could move your infected site elsewhere for diagnosis and, once done, use a backup to restore your site to an earlier point in time (or restore a remote backup to a different server and leave the original site for diagnosis).
Restoring a backup from a time when you 100% know that your website was not compromised can get your site back up and running very quickly.
With GridPane backups, you can choose to completely remove ALL website files or overwrite website files when running a restore. For malware, be sure to select the remove all option:
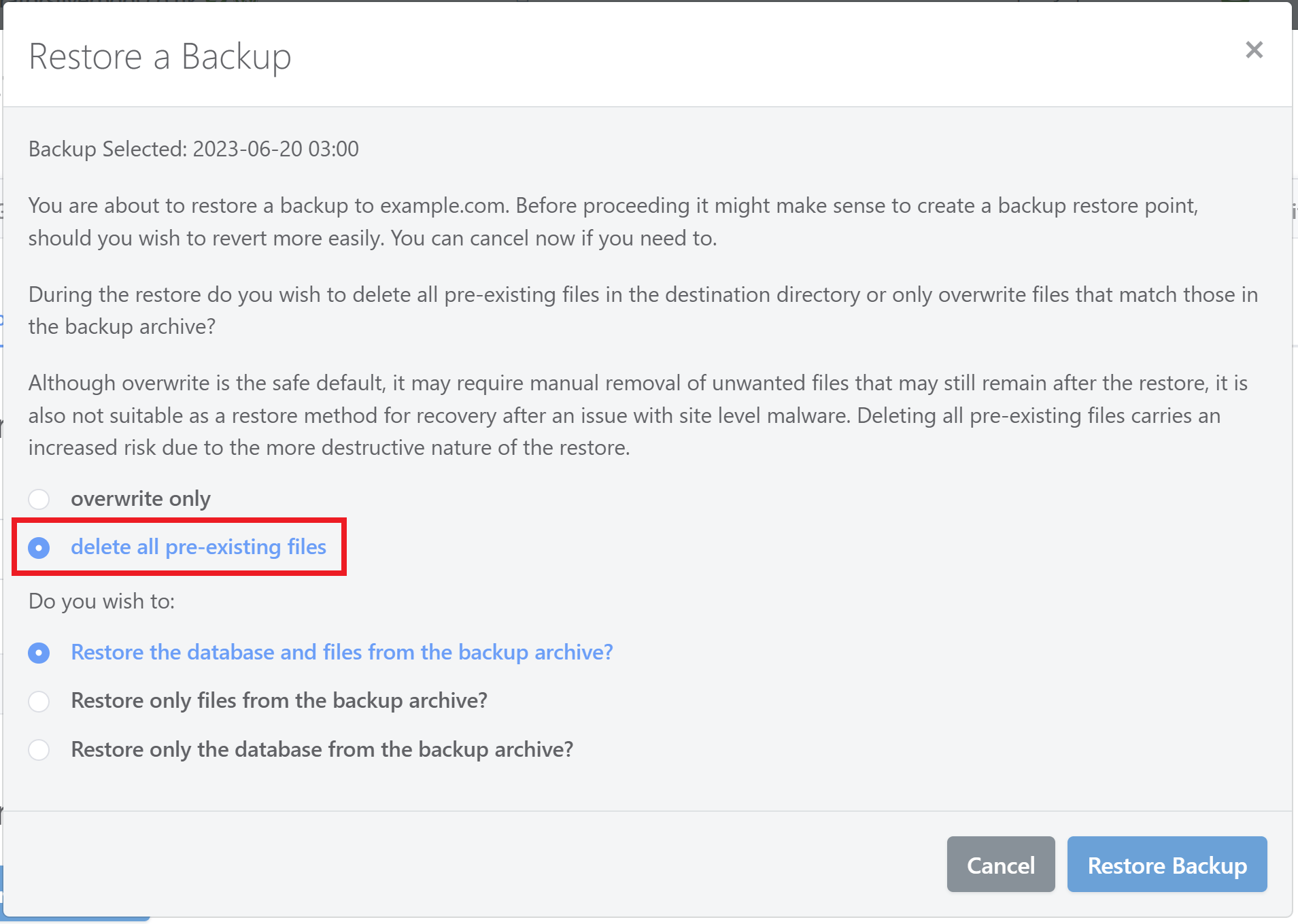
Once your site backup has been restored, you should then immediately run your core, theme, and plugin updates.
BEWARE: WordPress Security Plugins
You can learn about thoughts and recommendations for security plugins in this article:
Do I Need a Security Plugin When Using GridPane’s Security Features?
In recent months, Calvin Alkan of Snicco has published a great of information on how security plugins may not only have not protected you, they may have compromised your website’s security entirely.
False Sense of Protection
Security plugins can provide a false sense of security, and implementing security at the application layer is far less preferable to security at the DNS and server layers before malicious traffic even has a chance to reach your websites in the first place.
Many of the most popular security plugins have had extremely serious security vulnerabilities themselves, and there are numerous systemic issues in the WordPress security plugin space. Learn more here:
The state of WordPress security plugins in 2022
Malware Scanning
Plugin-based malware scanning in WordPress is flawed and conceptually impossible. If you have scanned a site with a security plugin and it’s returned no results, (or you’ve done some clean up but you’re still having issues) it may be because the malware has whitelisted itself within your scanner.
To learn more, check out this in-depth eye-opening research that explains why everything you know about your WordPress Malware Scanner is WRONG.
One-click Malware Removal
This will rarely work as intended. It’s possible that any infection you have may be simple to deal with, and in those circumstances, maybe these solutions will work. Putting your trust in these tools is a gamble, though, especially if the site is of any importance to a real world business.
